0CTF 2019 - Fast&Furious
·
CTF/2019
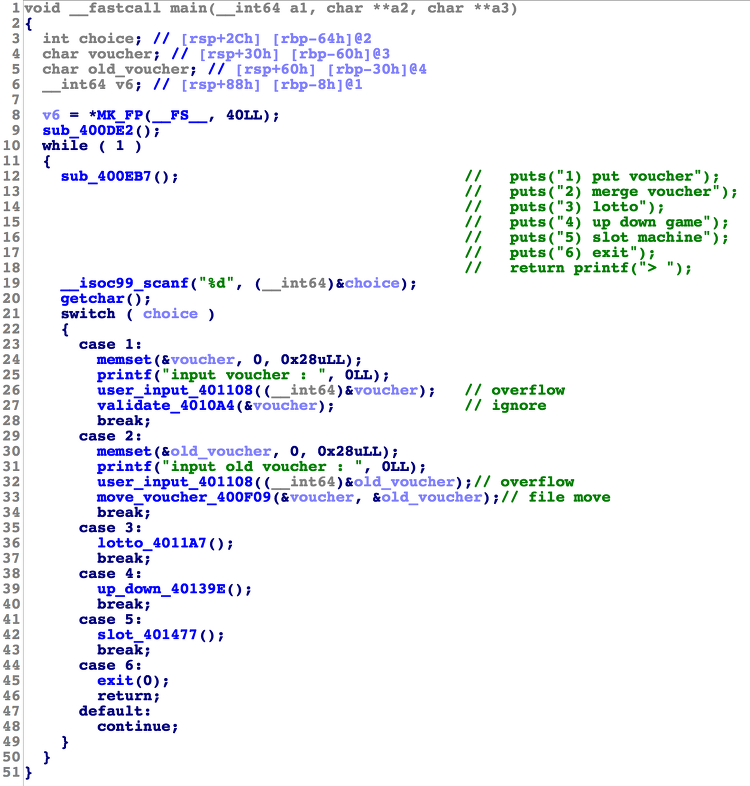
Fast&Furious Category : pwnable Summary : kernel module, use-after-free, null page dereference, memory leak, CVE-2019-9213Exploit #include #include #include #include #include #include //#define _GNU_SOURCE #include #include #include #include #include #include #include #include #include #include #include void *ptr; uint64_t user_cs; uint64_t user_ss; uint64_t user_rflags; uint64_t user_stack; int..