![]()
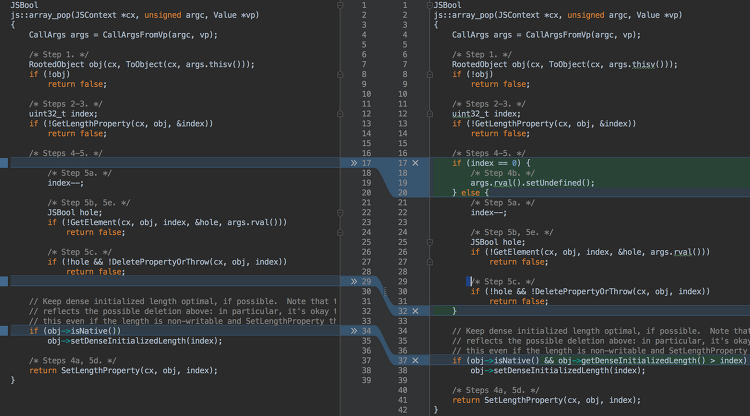
blackperl security blog에서 포스트 읽다가 기억난 김에 풀어본 문제.글 읽고 익스를 새로 짜봤다. https://bpsecblog.wordpress.com/2017/04/27/javascript_engine_array_oob/ Files -rwxr-xr-x 1 pwn3r pwn3r 5857384 Feb 12 2017 js -rwxr-xr-x 1 pwn3r pwn3r 95155 Feb 12 2017 jsarray.cpp -rw-r--r-- 1 pwn3r pwn3r 95297 Feb 12 2017 jsarray_original.cpp Mozilla의 SpiderMonkey Javascript engine을 취약하게 패치한 문제.3개의 파일이 주어졌다. (1) 인터프리터 (2) 패치 된 js..
![]()
Category : pwnable host : pwn1.chal.ctf.westerns.tokyo port : 21638 Update(2018/09/02 11:55:00 UTC) BBQ BBQ.old libc-2.23.so Summary : uninitialized variable, manipulate heap chunks, unsorted bin attack 다른 풀이 방법도 있지만, unsorted bin attack으로 풀겠다고 고집부리다가 꽤 오래 걸린 문제.취약점은 간단하지만, heap chunk들을 잘 조작해야해서 exploit이 오래걸린다.그래도 이런 풀이로 풀 수 있는 문제 많을듯. god angelboy. 풀고나서 다른 풀이있나 write-up을 찾아봤는데 좀 지렸다. 나는 전혀 생각못한..
![]()
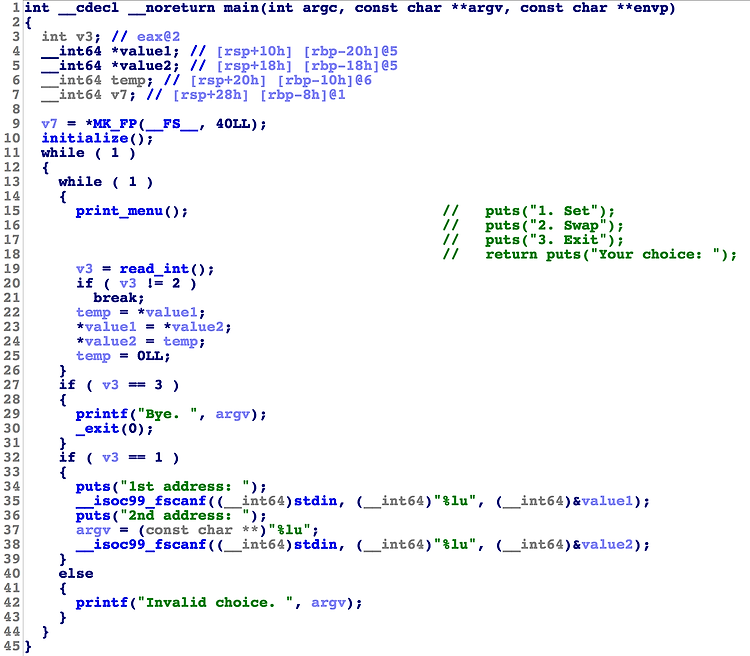
Category : pwnable SWAP SAWP WASP PWAS SWPA nc swap.chal.ctf.westerns.tokyo 37567 swap_returns libc.so.6 Summary : temp = *addr1; *addr1 = *addr2; *addr2 = temp; temp = 0 main 프로그램 자체는 굉장히 간단하며 2가지 기능이 존재한다. (1) set : 2개의 address를 변수에 입력(2) swap : 설정된 2 address가 가리키는 값을 서로 swap// temp = *addr1; *addr1 = *addr2; *addr2 = temp; temp = 0 user input과 got를 치환하면 좋겠지만, 2개의 address 말고는 입력받는게 없다.memory l..
![]()
Category : pwnable Hello Neighbor! nc neighbor.chal.ctf.westerns.tokyo 37565 neighbor_c libc.so.6 Summary : double staged format string attack, modify stderr->_fileno to 1(stdout) 1. Vulnerability 1.1. Format string bug 무한루프를 돌며 전역변수 format에 문자열을 입력받고 그대로 fprintf 함수에 넘긴다. (format string bug)stack에 control 가능한 값이 없으므로 double staged format string attack으로 원하는 주소를 stack에 만들어 덮어주어야 한다. 횟수에는 제한이 없기 때..
![]()
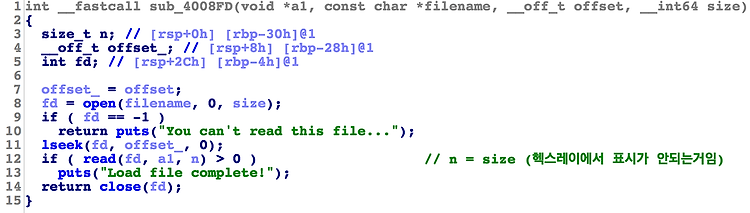
Category : pwnable host : pwn1.chal.ctf.westerns.tokyoport : 34835 Summary : stack bof, close(0);close(1);close(2), open("/dev/pts/0", O_RDWR) = 0, 1 Stack BOF size 제한이 없기 때문에, control 가능한 파일이 있다면 bof를 일으킬 수 있다."/proc/self/fd/0" 을 열면 0(stdin)으로부터 입력받는 것과 같은 효과.read(0, stack, n) 하는 꼴이 되어서 간단하게 eip control 가능. $ ./load Load file Service Input file name: /proc/self/fd/0 Input offset: 0 Input size: ..