![]()
Category : pwnable host : pwn1.chal.ctf.westerns.tokyo port : 21638 Update(2018/09/02 11:55:00 UTC) BBQ BBQ.old libc-2.23.so Summary : uninitialized variable, manipulate heap chunks, unsorted bin attack 다른 풀이 방법도 있지만, unsorted bin attack으로 풀겠다고 고집부리다가 꽤 오래 걸린 문제.취약점은 간단하지만, heap chunk들을 잘 조작해야해서 exploit이 오래걸린다.그래도 이런 풀이로 풀 수 있는 문제 많을듯. god angelboy. 풀고나서 다른 풀이있나 write-up을 찾아봤는데 좀 지렸다. 나는 전혀 생각못한..
![]()
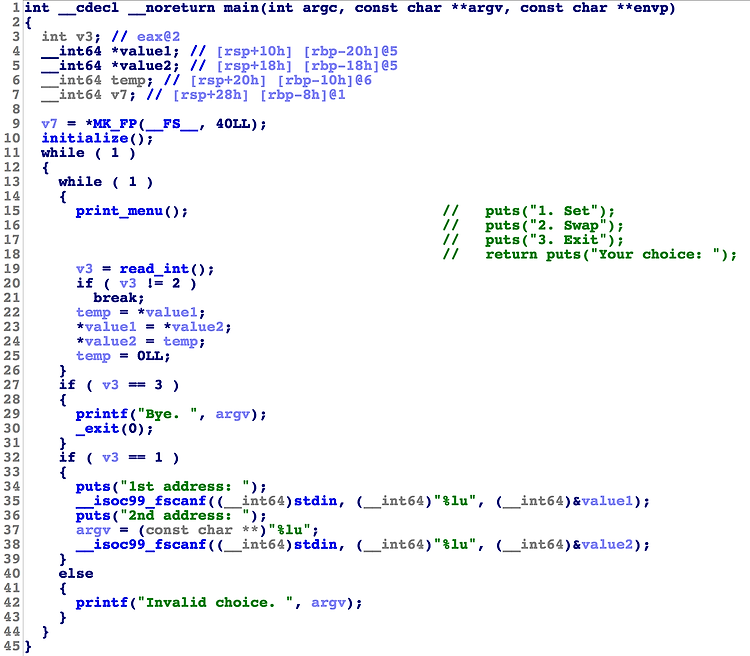
Category : pwnable SWAP SAWP WASP PWAS SWPA nc swap.chal.ctf.westerns.tokyo 37567 swap_returns libc.so.6 Summary : temp = *addr1; *addr1 = *addr2; *addr2 = temp; temp = 0 main 프로그램 자체는 굉장히 간단하며 2가지 기능이 존재한다. (1) set : 2개의 address를 변수에 입력(2) swap : 설정된 2 address가 가리키는 값을 서로 swap// temp = *addr1; *addr1 = *addr2; *addr2 = temp; temp = 0 user input과 got를 치환하면 좋겠지만, 2개의 address 말고는 입력받는게 없다.memory l..
![]()
Category : pwnable Hello Neighbor! nc neighbor.chal.ctf.westerns.tokyo 37565 neighbor_c libc.so.6 Summary : double staged format string attack, modify stderr->_fileno to 1(stdout) 1. Vulnerability 1.1. Format string bug 무한루프를 돌며 전역변수 format에 문자열을 입력받고 그대로 fprintf 함수에 넘긴다. (format string bug)stack에 control 가능한 값이 없으므로 double staged format string attack으로 원하는 주소를 stack에 만들어 덮어주어야 한다. 횟수에는 제한이 없기 때..
![]()
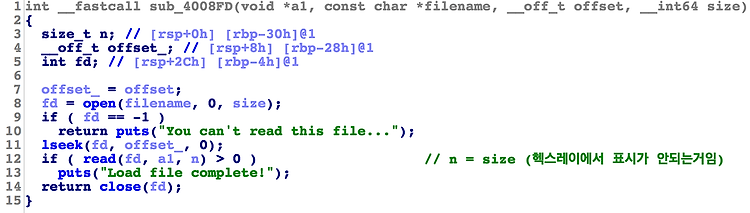
Category : pwnable host : pwn1.chal.ctf.westerns.tokyoport : 34835 Summary : stack bof, close(0);close(1);close(2), open("/dev/pts/0", O_RDWR) = 0, 1 Stack BOF size 제한이 없기 때문에, control 가능한 파일이 있다면 bof를 일으킬 수 있다."/proc/self/fd/0" 을 열면 0(stdin)으로부터 입력받는 것과 같은 효과.read(0, stack, n) 하는 꼴이 되어서 간단하게 eip control 가능. $ ./load Load file Service Input file name: /proc/self/fd/0 Input offset: 0 Input size: ..
https://github.com/kraj/glibc/blob/master/malloc/malloc.c 몇 부분만 정리 void *__libc_malloc (size_t bytes){ mstate ar_ptr; void *victim; void *(*hook) (size_t, const void *) = atomic_forced_read (__malloc_hook); if (__builtin_expect (hook != NULL, 0)) return (*hook)(bytes, RETURN_ADDRESS (0));#if USE_TCACHE /* int_free also calls request2size, be careful to not pad twice. */ size_t tbytes; checked_re..
Category : pwnable nc pwn03.grandprix.whitehatvn.com 2023file: material.grandprix.whitehatvn.com/pwn03Note: libc has been modified Summary : uninitialized variable leads to bof, redsled with vsyscall, modified libc (contains special gadget), close(0);close(1); Process(1) PoW 과정에서 stack 에 입력받는 데이터로 나중에 uninitialized variable를 control 가능.(2) uninitialized variable이 read의 size로 사용돼서 system(0) 호출시켜서..
Category : pwnable Summary : simple heap overflow, fastbin dup into stack 그냥 fastbin문제. 헬게이트 문제로 기억했는데 다른거였나봄.. 하지만 이상한 삽질하다가 시간 더 걸린거 반성하기.malloc_hook에서 원가젯 바로 못 쓰면 다른 hook 연동해서 간단하게 rsp 컨트롤하기.malloc 인자 뭐들어가는지 제대로 기억하기. ex.py#!/usr/bin/python from pwn import * def cmd_add(key_len, title, key): ru('>> ') ss('1') ru('Input key length...') ss(str(key_len)) ru('Input title...') ss(title) ru('Input ..
Category : pwnable nc pwn02.grandprix.whitehatvn.com 8005file: material.grandprix.whitehatvn.com/pwn02 Summary : simple uaf, libc-2.27.so, tcache poisoning 2 ways to exploit (1) simple uaf#!/usr/bin/python from pwn import * def cmd_add(title, brief_size, brief, refer, best): ru('Your choice') sl('1') ru('Title:') sl(title) ru('Enter brief size') sl(str(brief_size)) ru('Enter brief:') sl(brief) r..